PS Connection security
Configure HTTPS certificate
A custom certificate that is trusted by all client computers should be configured for MyQ Print Server. Three modes of certificate management are available:
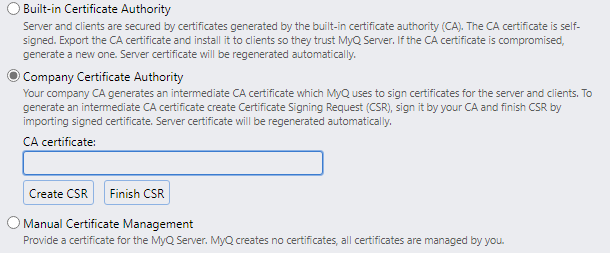
By default, MyQ Print Server creates its own root CA certificate and uses it to sign server and client certificates. The public portion of this certificate can be exported and deployed to the client certificate trust store, e.g., by using Group Policy or MDM.
Organizations with their own PKI already trusted might prefer the second option. MyQ Print Server uses its own intermediate CA to issue server and client certificates. The autogenerated intermediate CA certificate must be signed by the company’s CA so that it is trusted by clients.
If the corporate security policy does not allow for an intermediate CA certificate to be installed on MyQ Print Server, or a certificate issued by a public certificate authority is to be used, manual certificate management must be used instead.
Regardless of the CA mode, certificates are physically stored in the “C:\ProgramData\MyQ\Cert” directory, which may contain the following files:
server.pfx – server certificate with both public and private keys
server.cer – server certificate with public key
server.key – server private key
ca-root.crt – company root CA certificate with public key
ca-myq.pfx – issuing CA certificate with both public and private keys
ca-myq.crt – issuing CA certificate with public key
ca-myq.key– issuing CA private keys
Private keys of the local issuing CA (used in the first two modes of operation) are always protected by a randomly generated password that is stored in the internal Firebird database in an encrypted form.
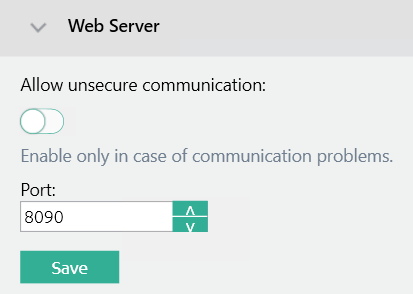
Block unencrypted HTTP traffic
Unencrypted HTTP traffic should not be enabled in the MyQ Print Server configuration:
Review communication security settings
Check the minimum security TLS versions configured in Settings – Network – Minimum TLS version. The default since MyQ X 10.2 is TLS 1.2.
For more advanced options, such as how to set the minimum required TLS to 1.3 instead, check Advanced Security.
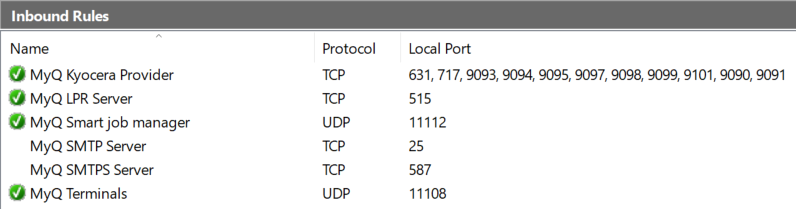
Block unused ports
Decrease the attack surface by disabling firewall rules for protocols not used by MyQ Print Server:
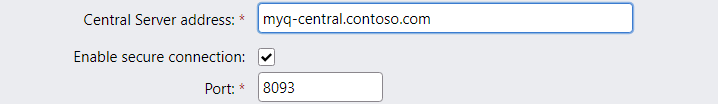
Encrypt connections to MyQ Central Server
Only use HTTPS to connect to MyQ Central Server:
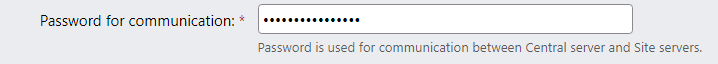
Use strong passwords for server-to-server authentication
Password for communication between central server and site should be strong (password complexity):
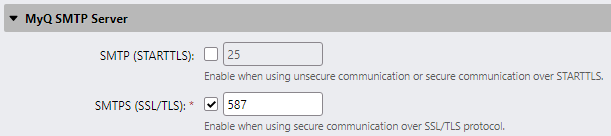
Secure SMTP traffic
When the SMTP protocol is used to send emails or to receive documents from network scanners, TLS encryption should always be enforced to ensure data confidentiality.
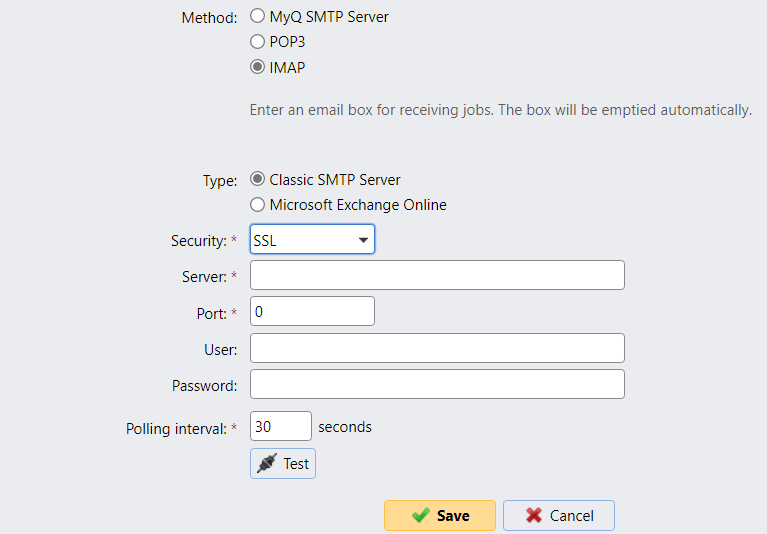
TLS encryption should also be enforced when the IMAP protocol is used, while the legacy POP3 protocol should be avoided:
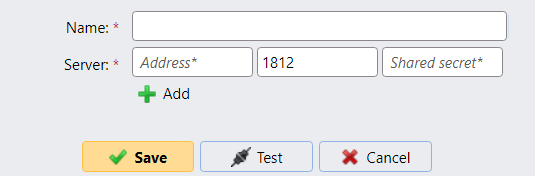
Use strong and unique RADIUS passwords
If RADIUS authentication is used, always generate strong shared secrets that are specific to the MyQ Print Server:
Encrypt LDAP traffic
TLS encryption should be used to secure all LDAP traffic:
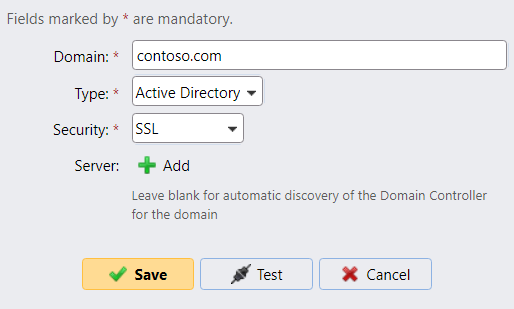
For security reasons, do not use START TLS, as it is vulnerable to MITM attacks. A certificate issued by a trusted CA must be configured on all LDAP servers (Active Directory domain controllers).
Secure SNMP traffic
Insecure SNMPv1 communication with devices should be avoided:
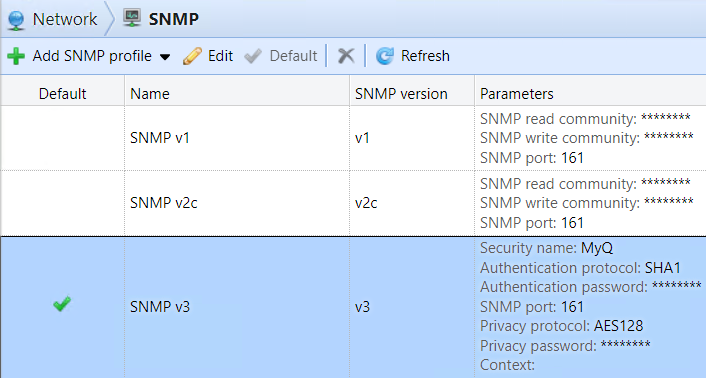
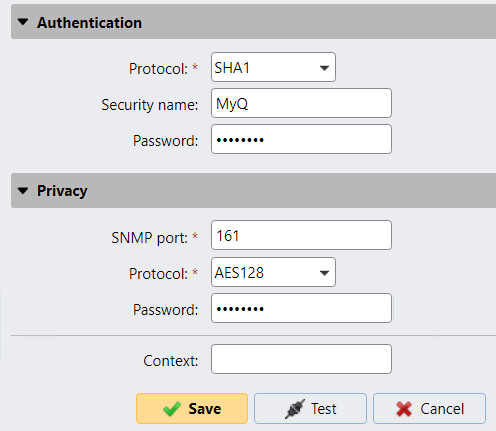
Only use SNMPv3 with a strong password and configure more secure cryptographic algorithms to be used (SHA1 and AES):
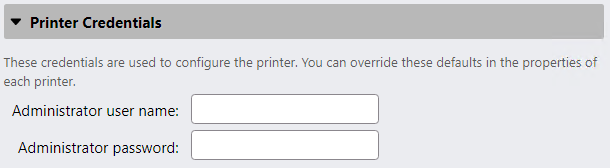
Secure printer credentials
Printer credential management is done outside of MyQ Print Server and is vendor specific. If possible, strong, randomly generated passwords should be used to manage printers:
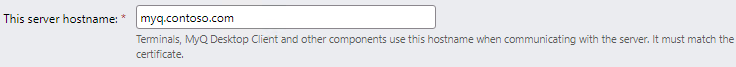
Always use FQDN
To prevent MITM attacks, strictly use fully qualified domain names in all configuration windows:
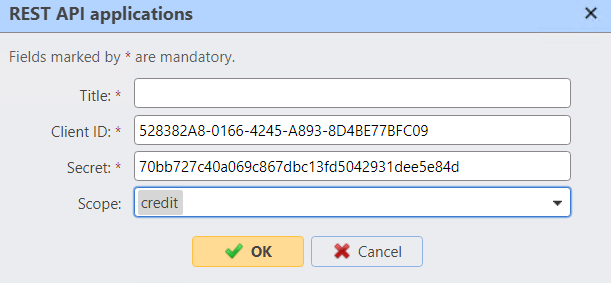
Protect REST API keys
When REST APIs are used, protect the client secrets from unnecessary exposure and perform periodic secret rollover:
.png)