Advanced Security
Security in print management is crucial as it involves managing sensitive documents and networked devices. Proper security measures help prevent unauthorized access to print jobs, ensuring confidentiality and compliance with privacy regulations.
Implementing secure print solutions, such as user authentication and encrypted communication channels, mitigates risks of data breaches through intercepted print jobs.
Advanced Security Configuration
The config.ini file can be used for further configuration of the MyQ Print Server. It contains sections with parameters and values for multiple settings, including security. For details, see Advanced Configuration.
We recommend that you consult with MyQ Support before editing the file.
Security Section
In MyQ X, communication security can be adjusted in various ways, providing maximum flexibility to suit any environment.
Security settings of the majority of components can be set with the config.ini file. Those components are HTTP Router, HTTP Server, SMTP, IPP, LPR, and Messages (WebSockets).
HTTP Components
For secure network communication, the HTTP Router is a key component.
While, e.g., the minimum SSL/TLS version configured in config.ini (see below) also applies to HTTP Router, it can be additionally configured with a file called traefik.custom.rules.yaml in more detail. The options set in the traefik.custom.rules.yaml file take precedence over the config.ini settings.
Secondly, the HTTP Server uses settings from the httpd.conf file.
When editing the HTTP Router settings, make sure you work with the file traefik.custom.rules.yaml in C:\ProgramData\MyQ, and not with the files traefik.rules.yaml and traefik.yaml in C:\Program Files\MyQ\Server that contain the installation defaults, and are reverted after every MyQ X upgrade.
Common Security Settings
Minimum TLS version
To specify the minimum security protocol used for communication, go to C:\ProgramData\MyQ and open the config.ini file in a text editor.
Add a section called [Security] and in a new line under that, add the parameter sslProtocol with the value you want. The possible values are TLS1, TLS1.1, TLS1.2, and TLS1.3.
From MyQ Print Server 10.2, the default value is TLS1.2.
For example, you can add:
[Security]
sslProtocol=TLS1.3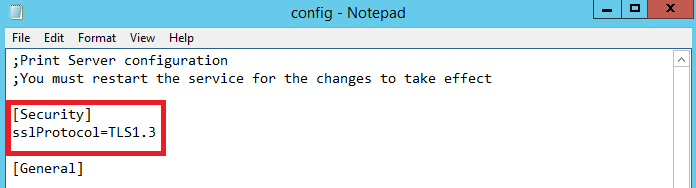
This applies to all components mentioned above, including the HTTP Router, and thus improves the overall communication security of the entire system.
Save the file and restart all services for the change to take effect.
Supported Cipher Suite
A full list of supported ciphers is available here.
You can also modify the set of supported ciphers alongside the TLS version.
You can do so with the following options:
Use strict secure defaults
You can use the config.ini flag sslCipherSuites to enable the strict secure mode. It uses the defaults of the HTTP Router component (and compared to the standard behavior, it deprecates ciphers considered weak).
This flag supports these options:
compatible
Enforces support of selected weak ciphers; might be needed for communication with older devices.strict
No weak ciphers allowed.
[Security]
sslCipherSuites=strictCiphers allowed in the compatible mode and not in the strict mode are:
TLS_RSA_WITH_AES_128_CBC_SHATLS_RSA_WITH_AES_256_CBC_SHATLS_RSA_WITH_AES_128_GCM_SHA256TLS_RSA_WITH_AES_256_GCM_SHA384TLS_RSA_WITH_3DES_EDE_CBC_SHATLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
While it is recommended to always prefer the strict mode that disables weak ciphers, it is not currently MyQ X’s default mode.
By default, MyQ X operates in the compatible mode due to the nature of printing systems, device support, and general update availability. Many still supported printing devices do not have (and might never have) available updates compatible with the strict mode.
Allow only selected ciphers
By editing traefik.custom.rules.yaml, you can specify what ciphers will be allowed by the HTTP Router during communication.
Example use:
tls:
options: { default: { cipherSuites: [ TLS_RSA_WITH_AES_256_GCM_SHA384, TLS_RSA_WITH_3DES_EDE_CBC_SHA ] } }When sslProtocol is set to allow only TLS 1.3, no ciphers can be disabled or specifically enabled. Secure defaults given by the HTTP Router defaults are used.
Make sure that the connected devices support the required ciphers, and if not, look up available firmware upgrades that may bring security improvements.
Force Kerberos-Only Authentication
For environments that require the strictest security, you can configure MyQ to use Kerberos only. This disables NTLM fallback for MyQ applications and enforces Kerberos-only authentication.
To configure this, in the [Security] section of the server config.ini file, add the following parameter:
KerberosOnly=true
Important! Ensure that your environment is correctly configured for Kerberos, including proper SPN registration.
.png)