Authentication Servers Settings
MyQ can integrate with your domain directory to synchronize users and groups, and enable authentication. This ensures that your current users and groups can interact with MyQ embedded terminals, web interface, and clients with their domain identity.
The following authentication methods are supported:
LDAP Server
Active Directory
Google Workspace
OpenLDAP
Novell
Microsoft Entra ID
Radius Server
In Settings > Authentication Servers you can configure the following:
Synchronize users from and/or have them authenticate towards an LDAP server, such as a local Active Directory domain.
Synchronize users from your Microsoft Entra ID, and use Sign in with Microsoft for the MyQ Web Interface, Mobile, and Desktop Clients.
Authenticate users against a Radius server.
Synchronize and authenticate users and groups from Google Workspace with Secure LDAP.
You can later assign the authentication server created here to be used by all synchronized users automatically when you are creating the user synchronization source.
You also can control these settings for each user individually in their profile on the Users page.
If you only authenticate users against MyQ (ID cards, PINs, and passwords), and thus do not use any remote authentication servers, or need to integrate with another external authentication provider, see User Authentication for details.
Limitations
Users using an LDAP, Microsoft Entra ID, or Radius authentication server cannot sign in on the MyQ Web User Interface with a PIN. However, they can use their PIN on the MyQ Embedded terminals and MyQ Desktop Client up to version 10.0.
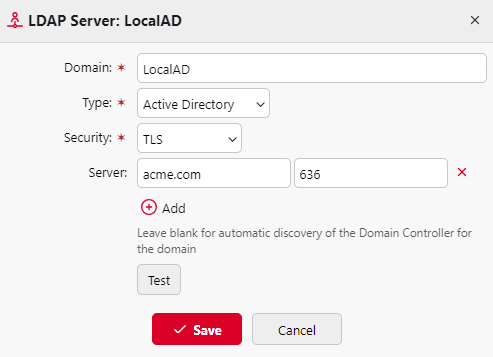
Add an LDAP Server
Go to MyQ > Settings > Authentication Servers, click +Add, and select LDAP Server.
The LDAP server properties panel opens.Enter the LDAP domain in LDAP format (for example,
dc=example,dc=com).Under Type, select the appropriate LDAP server:
Active Directory, or
another supported option such as Novell, OpenLDAP, or Google Workspace.
Configure the security settings:
Select the security protocol for the LDAP connection.
For Active Directory, you must select TLS.
Configure the server connection:
Enter the server hostname and port.
For Active Directory with TLS, use port 636.
If the hostname or IP address is unknown, you can leave it empty to allow automatic server discovery.
To define multiple addresses for the same LDAP server, click Add.
(Google Workspace only)
When Google Workspace is selected:Default values for Security, Server, and Port are filled in automatically.
In the Certificate section, click Add and upload the certificate file (
.crt) and private key file (.key) obtained from the Google Admin console.
Click Save to add the LDAP server.
(Optional) Click Test to verify the connection, and enter the LDAP client username and password when prompted.
Add Microsoft Entra ID Server
Click +Add and select Microsoft Entra ID Server. The new Microsoft Entra ID server properties panel opens on the right side of the screen.
If you have already added Microsoft Entra ID in the Connections settings, the server appears on the list. If not, click Add new, add the Microsoft Entra ID connection first (follow the guide for creating a new Entra ID connector).
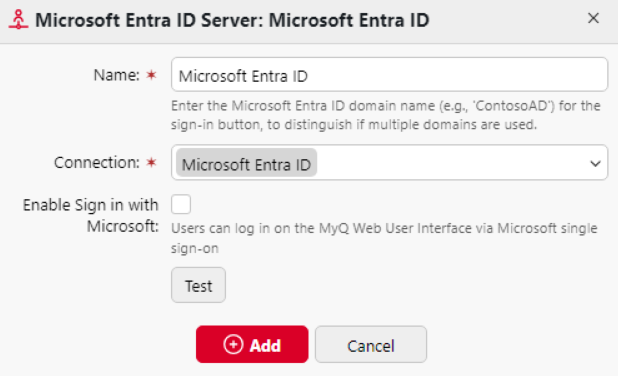
Check the Enable Sign in with Microsoft checkbox if you want to allow users the login method Sign in with Microsoft.
Click Save. The Microsoft Entra ID Server now appears on the list of servers.
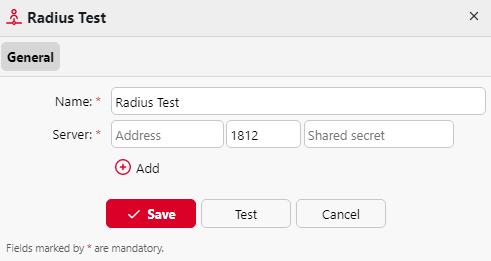
Add a Radius Server
Click +Add and select Radius server. The new Radius server properties panel opens on the right side of the screen.
Enter the Radius server Name.
Enter the Server IP address or hostname, the communication port and the Shared secret.
If you have more addresses related to one Radius server, you can add them by clicking Add.
Click Save. The Radius server now appears on the list of servers.
When an authentication server is renamed, a server with the old name will still appear in the Authentication server settings of a user profile, alongside the server with the new name. The old server is removed after the following user synchronization propagates changes.
.png)