Synchronize Users from Active Directory
MyQ X offers synchronization from Active Directory via the LDAP protocol. As a result, the administrator can benefit from the advantage of defining the organizational units they want to synchronize, synchronizing not only the users' details, but also their group membership, and even synchronizing users from multiple domains.
Before you start synchronizing Active Directory users, you should determine the specifics of print job authentication in your environment.
Overview
To synchronize users from Active Directory, complete the following steps:
User Detection from Print Jobs: Determine how to optimally authenticate incoming print jobs in MyQ.
Configure Active Directory synchronization: Create LDAP synchronization source(s) to import users from AD to MyQ.
Adjust Synchronization to your environment: Synchronize additional user information to properly identify print jobs, allow synchronization with ID Cards stored in Active Directory, and more.
Decide on User Detection Method
Follow the recommendations in the Identify Job Authentication Method to determine how your users are recognized. This step is vital for ensuring the successful configuration of user synchronization.
If the detected user from your testing aligns with the user’s sAMAccountName, you are ready to synchronize users.
If the detected username differs, check the AD attributes to identify the correct one. Read below what steps to take if the identifier is the userPrincipalName or another AD attribute.
Configure Active Directory Synchronization
To start synchronizing users into MyQ X, you will set up the following:
Create an Active Directory LDAP authentication server: This means adding the server and its connection details into MyQ.
Create an Active Directory LDAP synchronization source: Here you select the created authentication server in Step 1 and configure the options under which you want to synchronize groups and users.
For step-by-step instructions on how to set up an LDAP authentication server and synchronization, follow these guides:
Print Server: User synchronization from LDAP servers
Central Server: User synchronization from LDAP servers
Base DN
The syntax of the Base DN depends on your configuration and the target LDAP server. It also might be required or preferable to leave it empty.
Example Base DN:
DC=company,DC=netMapping Attributes in MyQ
As part of the setup, you will select Active Directory parameters that will be synchronized into user profiles.
If you leave the AD’s LDAP properties empty, MyQ by default will use these attributes:
Default Properties
MyQ user property | AD attribute |
|---|---|
Username |
|
Fullname |
|
|
Other parameters, such as Alias, Personal number, Notes, Language, User's storage, Card, and PIN do not have default fields defined to read values from.
Use User Principal Name (UPN), MailNickname, or Other Parameters to Identify Users
When setting up the LDAP synchronization, you may have noticed that there is no option to define the LDAP attribute to be used as a username. That is because, as mentioned earlier, MyQ always uses the sAMAccountName for a username.
If your job senders are recognized by their UPN (userPrincipalName), you can use this attribute in the Alias field, and once synchronized, the UPN will also be used for job authentication.
User Authentication with Alias
Users in MyQ can use both, usernames and aliases, for logging in. Meaning, if you set userPrincipalName as an alias for users, they can also log in to MyQ with it.
In many environments, the UPN is equal to the work/business email address. It might be convenient for your users to use their UPN instead of having to remember something different such as sAMAccountName if it differs from the credentials they use in other company systems.
Similarly, a parameter containing an email address may be used as the user’s alias.
Synchronize User’s Home Folder
If users in your organization have their own dedicated secured local folder, you can synchronize these paths for each user in the User’s storage MyQ attribute. This information might be stored in the HomeDrive AD attribute.
Once synchronized, this folder can be used in various places in MyQ, especially in the Terminal Actions settings. You can set up Easy Print from the user’s storage as well as Easy Scan to the user’s storage. Such actions will automatically use the storage of the currently signed-in user when printing and scanning on the Embedded Terminal.
Multiple AD Domains for Synchronization and Authentication
MyQ X lets you add up to 5 LDAP authentication servers. This can be useful for organizations with more complex infrastructure.
We dedicated an article to such scenarios where we explain how to set up such synchronization and prevent username clashes, see Local Multi-domain Environments (Active Directory).
Synchronize Attributes from Multi-value Fields
Sometimes data such as ID cards or personal numbers can be combined into one Active Directory attribute. In such cases, it is possible to apply a transformation with regular expressions on these fields in the settings of the synchronization source – Transformation section.
Example:
If the ID card number is stored together with the user’s personal number such as 288373;736, use transformation to parse only the value before ; in the field to be used as the ID card.
For detailed configuration and examples of regex settings, please see Regular Expression Transformation for User Synchronization.
Security Recommendations for Active Directory
Active Directory (AD) and Lightweight Directory Access Protocol (LDAP) are essential technologies for managing identities, authentication, and authorization in numerous organizations. Securing these systems is crucial to safeguard sensitive information and uphold the integrity of IT infrastructures.
As the key security features, organizations should focus on Encryption, Access Control, Audit and Monitoring, and Least Privilege Principle.
Encryption and Communication Security
LDAPS (LDAP over SSL/TLS) is highly recommended. It can be enforced in the Authentication Server’s settings in MyQ X. Another available option is StartTLS which is a command that upgrades a standard, unsecured LDAP connection (usually over port 389) to a secure one by negotiating the use of TLS (Transport Layer Security).
When communication over TLS is anticipated, the server where MyQ X is running must be able to verify the AD’s certificate issuer to trust its certificate and allow for secure communication. To achieve this, you need to install the issuing root CA in the certificate store of the given server where MyQ is running.
Confidential Attributes and Schema Extensions
AD offers many user attributes that might store away sensitive or private information about the individual. This applies especially to attributes that store user identifiers, e.g., ID Card numbers or even PIN codes – MyQ X allows the import of these values from AD over LDAP(S).
Without additional changes to the security of your AD, every domain user could potentially use their domain credentials to read these values in the directory for any user. Therefore, organizations must secure this data type and prevent it.
Here confidential attributes come into play. Certain attributes can be designated as confidential, with limited access granted only to specified trustees, while remaining entirely hidden from all other domain users. This trustee user account can be then provided to 3rd parties, including MyQ X’s Authentication Servers settings, for user synchronization.
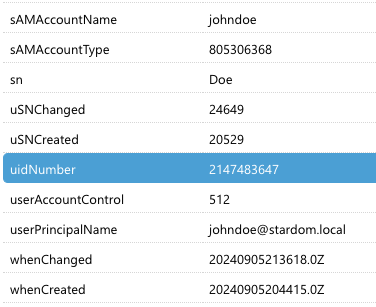
Example: User with permission to read uidNumber
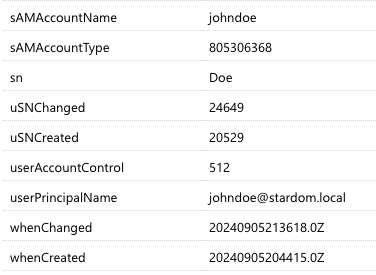
Example: User lacking permission to read uidNumber
The Active Directory schema's standard attributes can be protected using this method.
However, for even better protection, the confidential flag can be applied on custom extension properties, which are fields not included in the standard schema. These custom properties are more difficult to interpret due to their customizable nature.
Please be mindful of the impact on your environment. Extending the AD schema is a significant change and should be done with caution. Once added, custom attributes cannot be removed, so careful planning is essential. It is recommended you test the changes in a lab environment before applying them to a production environment.
.png)