Security and Certificates
Proper configuration of security and certificates is essential for safeguarding sensitive data such as print jobs, user credentials, and administrative access.
General Security
MyQ X comes with certain default security settings. It automatically enforces an encrypted connection between the built-in HTTP proxy (and Web Server running behind the proxy) and other servers or clients, such as Embedded terminals, mail servers, SQL servers (in the case of the Central Server), and end-user devices.
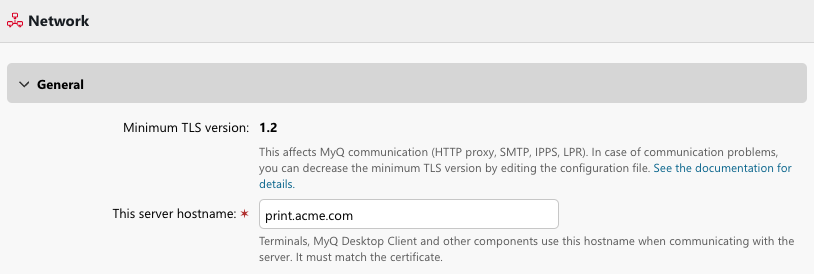
By default, the minimum TLS version required is 1.2.
Settings – Network Security Settings
The minimum required TLS/SSL version can be adjusted when needed, see Security settings in config.ini.
It is highly recommended you keep the default (1.2), or increase the minimum to TLS 1.3. The option to decrease the level of encryption is available only for edge cases when communication with old printing devices that do not support TLS 1.2 and higher is needed.
Certificates
Certificates are crucial in MyQ X by ensuring secure connections between print devices, servers, and user workstations through SSL/TLS encryption. Administrators in MyQ X can manage certificates centrally to enforce secure authentication and authorization for all users accessing print services. MyQ X supports the use of trusted third-party certificates, as well as internally issued certificates to enable flexible and scalable security configurations for different environments.
Trust Between MyQ X and Servers
To securely connect to external systems that MyQ X needs to interact with, you will need the MyQ server to trust the certificates of these remote servers and services. This is needed for HTTPS, SMTPS, LDAPS, and IPPS.
Since version 10.2, MyQ X is designed to automatically trust the Root CA certificates from the server’s system certificate store.
Certificates in Certificate Management (mmc.exe) > Trusted Root Certificate Authorities are exported into the cacert.pem file that sits in the ProgramData folder of MyQ X.
The certificate synchronization is performed during the Maintenance task run. For this reason, if you encounter problems with certificates, and you confirm that the correct certs are installed in the system, run the Maintenance task, and try connecting MyQ X to the remote system again.
This allows MyQ X to automatically trust certificates issued by imported CAs, which is particularly helpful when they are published by Group Policy or from Active Directory.
Before MyQ X 10.2 Update
For the majority of connections that were expected to be secured via SSL/TLS, it was already necessary that the remote server’s certificate was trusted by the system MyQ X was running on, and thus also by MyQ X.
For some operations, it could have been necessary to manually edit the cacert.pem, ldap.conf or .ldaprc files and include necessary (especially Enterprise) CA certificates. The reason was that certain connections and components utilized a different certificate store rather than the system one.
Trust Between MyQ X and Connecting Clients
Read how to select the server certificate that MyQ X presents to clients to secure communication. You will need this to:
Serve your users the MyQ Web Interface on HTTPS.
Communicate securely with printers and MFDs and the Embedded terminals installed on those devices.
Connect to the server with the Desktop Client operating in the “Strict” mode.
Print securely via IPPS.
Connect and print with the Chromebook Extension.
Connect securely from the Mobile Client for Android and iOS.
The Settings - Network page is where you manage certificates. This applies both to the Central Server and Print Server. In these settings, you have three modes available:
Built-in Certificate Authority
MyQ creates a self-signed CA certificate and uses it to sign server and client certificates.
To use these certificates in production environments, you need to distribute the CA (which can be exported on the Network page) to all clients that will be connecting to the server. This is feasible for organization-managed devices where this certificate can be distributed with Group Policy or Intune.
However, in case BYOD devices are expected to connect, you have to provide the users with an option to download and install the MyQ Certificate Authority manually. Otherwise, they will be getting warnings that the connection/server cannot be trusted and Embedded terminals will not function properly.
Company Certificate Authority
Your company CA generates an intermediate CA certificate which MyQ uses to sign certificates for the server and clients.
Since this certificate authority (CA) is probably a custom enterprise CA, similar conditions apply as for the built-in self-signed certificate. The CA will need to be distributed to devices that your organization can manage, or made available for end users to install themselves.
Manual Certificate Management
Provide a certificate for the MyQ Server. MyQ creates no certificates; all certificates are managed by you.
It is expected that you have previous experience with certificate management and that you have issued a certificate for the MyQ server and signed with your own Certificate Authority. This can be a publicly trusted CA (such as Let’s Encrypt, GlobalSign, etc.), or a CA created with Active Directory Certificate Services (AD CS) in your domain.
Bring-Your-Own-Devices and Certificates
Compared to managed environments, such as a Windows domain, certificates for BYOD and devices not joined to a local domain or Entra tenant are a more complex issue.
If you expect to commonly serve printing services to guest users and visitors, or your organization is considered a public service (schools, libraries, traffic hubs, etc.), consider signing your server certificates by a publicly trusted CA that is already included in desktop and mobile operating systems and browsers out-of-the-box.
Certificates and Embedded Terminals
During remote setup when the Embedded terminals are installed, the MyQ X server uploads the CA certificate to the device, so that when MyQ X presents its certificate to the device, it is trusted. This is, however, possible only in the Built-in Certificate Authority and Company Certificate Authority modes.
In Manual Certificate Management mode, MyQ X does not get access to the CA certificate because it is not provided. Only the server certificate, which is signed by the CA, is uploaded. The CA certificate needs to be added to the devices manually.
Some vendors or devices might have stricter rules for certificate validation, e.g., they can require the certificate to contain the full FQDN (Fully Qualified Domain Name; such as print.acme.com), or the device might reject wildcard certificates (such as *.acme.com).
Always follow the manual, instructions, and recommendations for that particular vendor. The requirements for certificates may differ from device to device. Uploading certificates automatically may not be also available for all vendors. In case of problems, consult with your MyQ X provider.
.png)