Data security
Restrict data folder permissions
The data folder of MyQ Central Server contains highly sensitive data, including the user database and TLS certificate private key. Its current location is displayed in the MyQ Central Server Easy Config application:
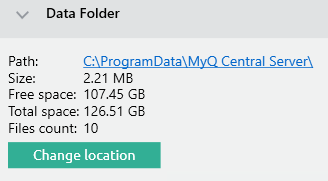
All users (local/domain) have read access by default:
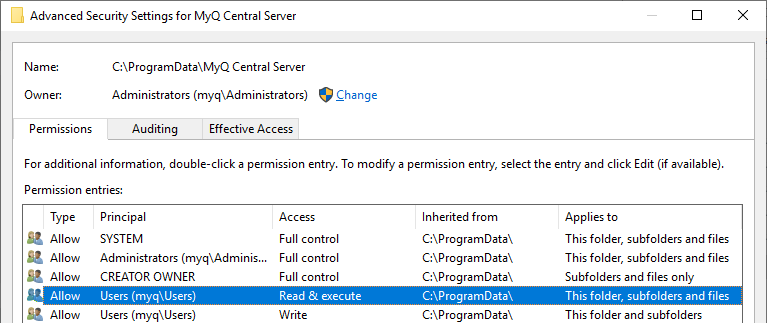
Only Administrators, SYSTEM, and MyQ service account should have access to this directory. Here is a sample batch script that can be used for permission hardening:
@ECHO OFF
REM Add the virtual account SIDs to all MyQ Central Server services:
sc sidtype myqm_platform unrestricted
sc sidtype myqm_apache unrestricted
sc sidtype FirebirdServerMasterInstance unrestricted
REM Grant rights to the virtual service accounts:
icacls "%ProgramData%\MyQ Central Server" /grant:r "NT AUTHORITY\SYSTEM:(OI)(CI)F" /grant "BUILTIN\Administrators:(OI)(CI)F" /grant "NT SERVICE\myqm_platform:(OI)(CI)M" /grant "NT SERVICE\myqm_apache:(OI)(CI)M" /grant "NT SERVICE\FirebirdServerMasterInstance:(OI)(CI)M"
/inheritance:r /Q
Enable database encryption
When using the embedded database, always encrypt it using a custom certificate to lower the risk of data leaks:
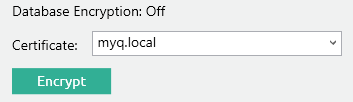
The certificate needs to have the “Encrypting File System” Enhanced Key Usage (EKU) and it must be located in one of the following computer certificate stores:
Personal
Trusted Publishers
Third-Party Root Certification Authorities
Other people
The Personal store is the preferred one.
Encrypt backups
Database backups should be protected by secure, randomly generated passwords:
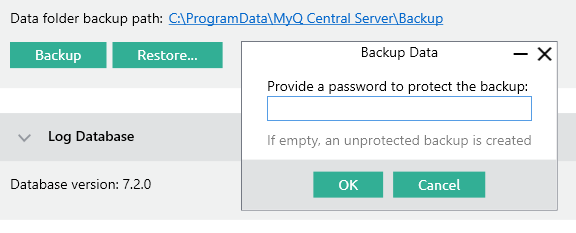
Enable disk encryption
If possible, a full disk encryption technology like Microsoft BitLocker should be enabled on the MyQ Central Server to protect the data at rest:

.png)